As a manufacturer of hardware wallets, the title of this article might seem a bit counterintuitive. Of course, our goal is not to steal bitcoin, but instead to equip people with the tools to make self-custody of their bitcoin both as easy and secure as possible. But from a user perspective, thinking about ways to steal bitcoin can actually be a very helpful exercise!
Adopting the mindset of an attacker can help to identify weak spots in your own defense and increase overall awareness of potential risks you might encounter during day to day use. To do exactly that, let’s explore a few of the most common attack methods – and how you can protect yourself from them.
Tricking someone into downloading a fake app
Fake wallet software can trick you into thinking you’re using authentic software from a reputable source by imitating their behavior and user interface. This can quickly create a false sense of familiarity, and is thus a very potent attack method.
There are several ways such software can find its way onto your devices, e.g. by manipulating search engine results, sending you malicious links or installing them in the background as part of another, seemingly unrelated software installation.
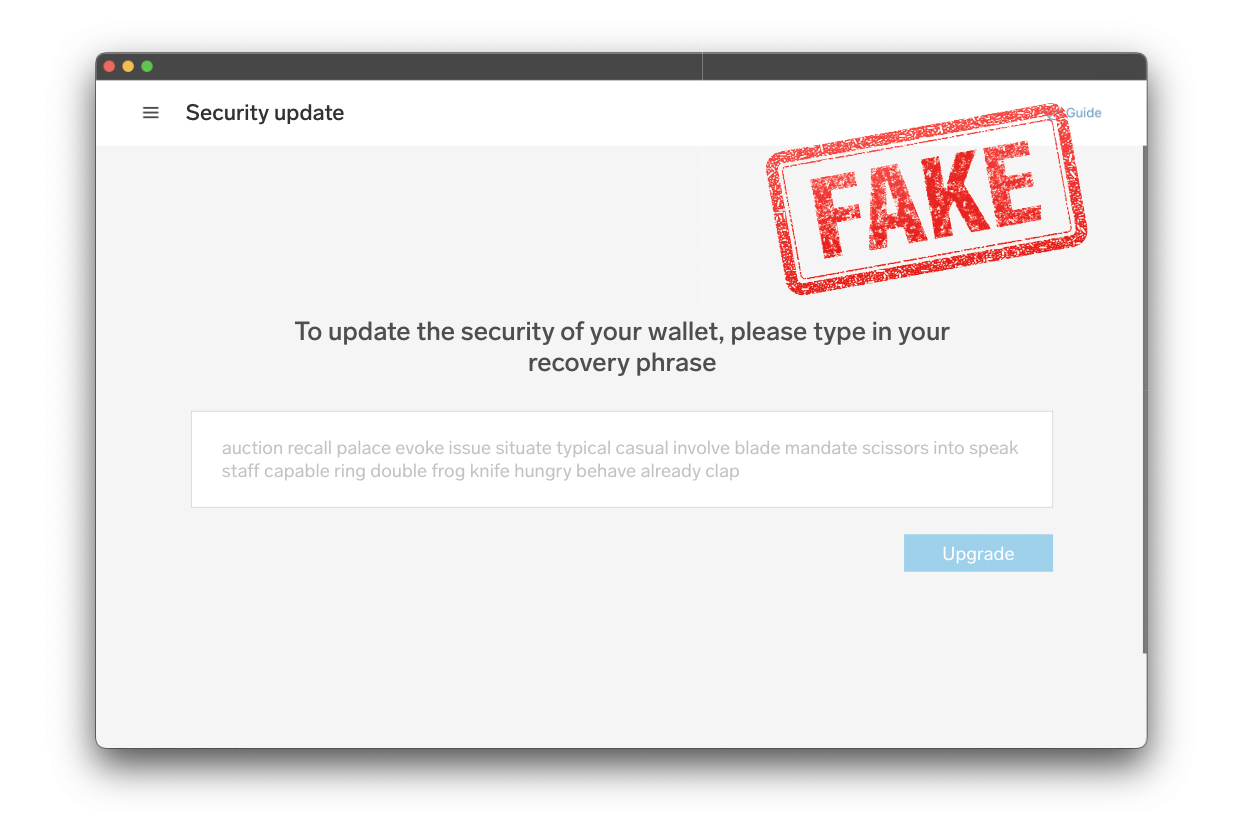
As will be the case with other attack methods, fake wallet software can differ in terms of how sophisticated the attack is planned out and implemented. In the example above, the attack is quite obvious, since the app is directly asking for recovery words, which should instantly alert most users, as they realise that the real BitBoxApp would never do that.
However, a fake version of the BitBoxApp – or any other wallet software for that matter – could in theory look exactly like its original, with subtle changes in the background that manipulate addresses or transaction amounts. But more on that later!
How to protect yourself
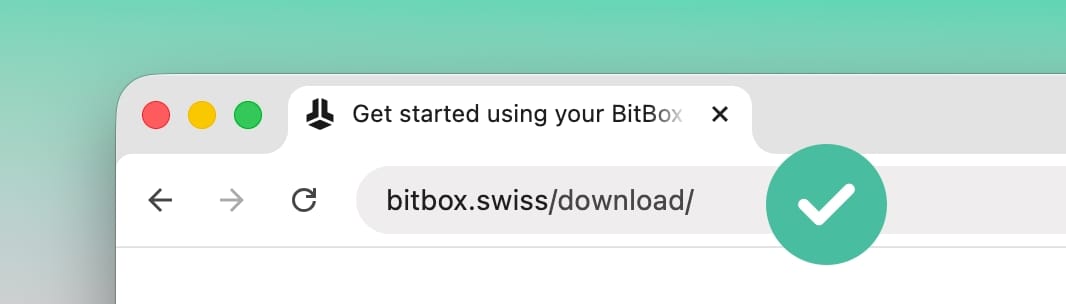
To avoid installing fake versions, always download wallet software directly from the developer’s official website. For the BitBoxApp, this would be bitbox.swiss/download. Even when downloading through the Apple App Store or Google Play Store, we recommend using the links on our website when you install them for the first time.
Verifying the domain of your browser’s address bar is a helpful step to ensure you’re in the right place. It can also make sense to bookmark official sites to prevent mistyping their URLs in the future, and to avoid using search engines when installing sensitive software, as their algorithm might serve you ads or wrong results, instead of the official website you’re looking for.
If you have the technical expertise, you can also verify the signature we provide for each app release to verify the authenticity of the BitBoxApp you downloaded; or alternatively verify the checksum matches.
Regardless of how careful you are about downloading software, keep in mind that you ultimately do not want to trust your smartphone or computer anyway. The hardware wallet and its display should always be the final and most important safety barrier when it comes to verifying addresses and transaction details. Even if you are using a very sophisticated fake app, the display of the BitBox will end up revealing the truth. This is exactly what hardware wallets are designed to do: keeping the private keys and the need to trust away from your host device.
Learn more about why a hardware wallet absolutely needs its own display.
Manipulating Bitcoin addresses
One of the most potent attack methods is the direct manipulation of receive addresses. It can affect almost anyone, no matter how secure the wallet setup is, since most interactions with receive addresses happen outside the secure environment of hardware wallets.
Address spoofing can come in different shapes and forms. Whether someone simply pretends to be a friend of yours, providing you with a fake receive address, or highly sophisticated attacks where malware switches out receive addresses silently in the background – using the wrong address leads to irreversible loss of funds.
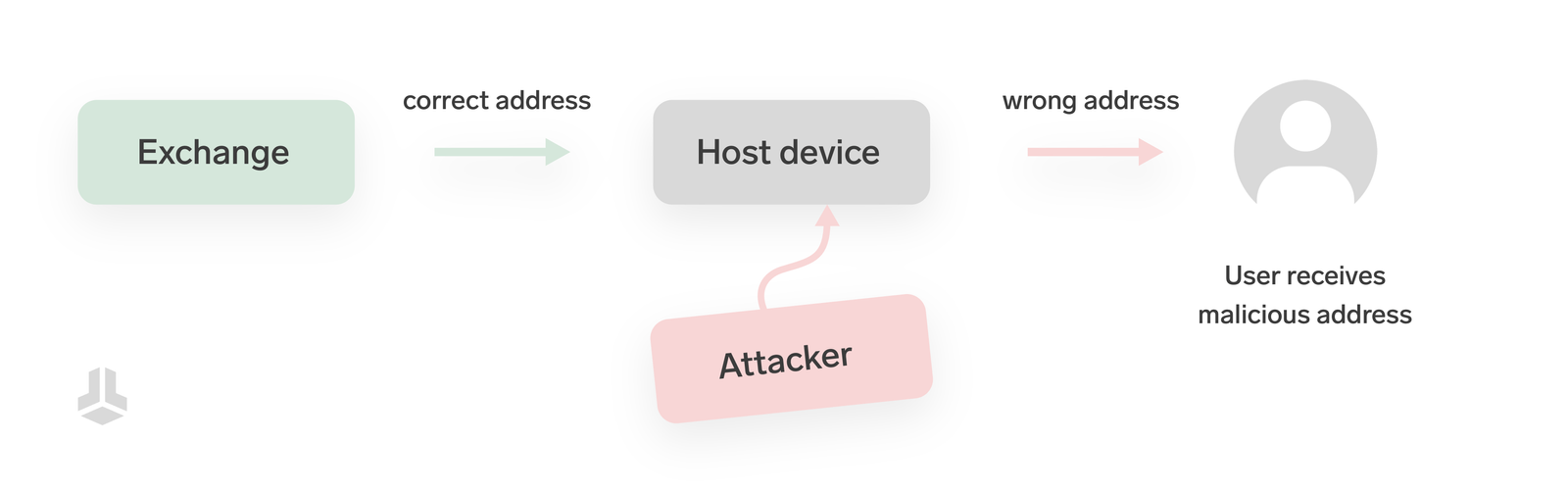
In a very recent example, a supply chain attack in the popular Node Package Manager (NPM) led to several packages used by developers across many applications being compromised with malware. Due to the nature of how such software packages are used, the malware was installed billions of times within the short timespan it was out in the wild. Its goal was to try and steal cryptocurrency by swapping out wallet addresses with ones that look similar – but belong to an attacker. Luckily, the attack didn’t go far in terms of successfully stealing funds, but it shows how quickly the possibility of address spoofing can become a real threat. The BitBoxApp and BitBox02 firmware were not affected by this vulnerability.
How to protect yourself
Protecting yourself against basic forms of address spoofing is fairly easy, but it requires a fair bit of diligence. What the attack ultimately comes down to is that you cannot trust your host device to verify whether a receive address belongs to your wallet or whether the host device is actually using the correct address you want to send bitcoin to.

This is why you should always compare the Bitcoin address shown on your hardware wallet with where it came from or goes to. For example, when sharing a new receive address with an exchange, compare the address on the device with what you actually ended up pasting in the browser. Equally, when someone sends you an address, compare what’s shown on the BitBox with where you originally received this address from.
Make sure to compare a majority of the characters in the Bitcoin address. The popular advice to “only check the first and last characters” is not always good enough, since there are ways to manipulate addresses to look visually similar in certain areas (e.g. by leveraging Levenshtein distance). In fact, clever address manipulation like this was part of the aforementioned NPM package vulnerability as well.
Sending securely
Achieving 100% certainty that an address you’re sending bitcoin to is correct is very difficult. This is because the integrity of the address not only relies on your host device, but the entire communication channel you were using to receive it in the first place. To further reduce the risk of sending to the wrong address, you can verify the address additionally through an independent communication channel (e.g. by using a different device or messenger).
We took things even further and implemented payment requests in the BitBox02 firmware to make selling bitcoin with our partner Pocket Bitcoin more secure. This way, the BitBox can cryptographically verify an address came directly from Pocket and was not changed in the process – without trusting the host device.
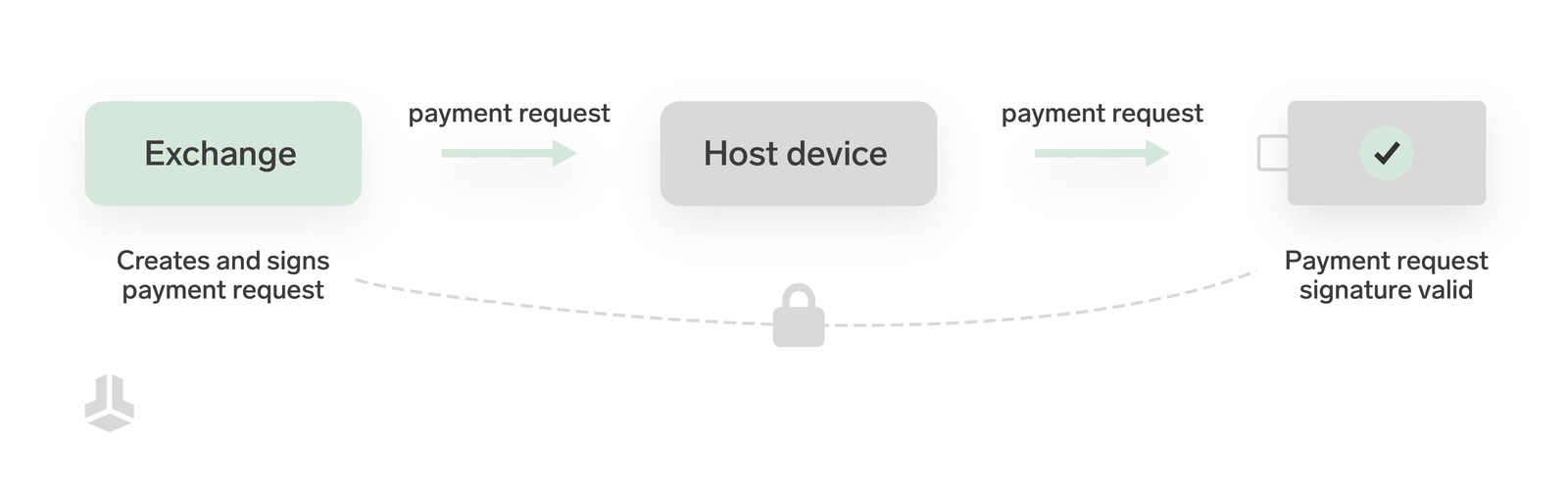
Sending scam emails
Phishing is as old as the internet itself, and bitcoin is no exception. Scam emails and social engineering as a more general umbrella term are unfortunately still very effective. This is mainly due to how easily scalable such attacks are: Sending emails to thousands of people or impersonating someone on Telegram is quickly done and does not come with huge upfront costs for attackers. Even if just a small number of the recipients bite the bullet and make a mistake, it may be enough to make the attack profitable.
How to protect yourself
If anyone ever asks you for sensitive wallet information, such as your recovery words, all of your internal alarm bells should instantly go off, no matter how legitimate their message may seem – and even if you know them personally.
This especially applies to fake messages you might receive from hardware wallet manufacturers. If you receive an email or Telegram message from “BitBox Support” asking for your recovery words because of an “important security update”, it is guaranteed to be a phishing scam and you should ignore and delete the message right away, without clicking any links or loading attachments.
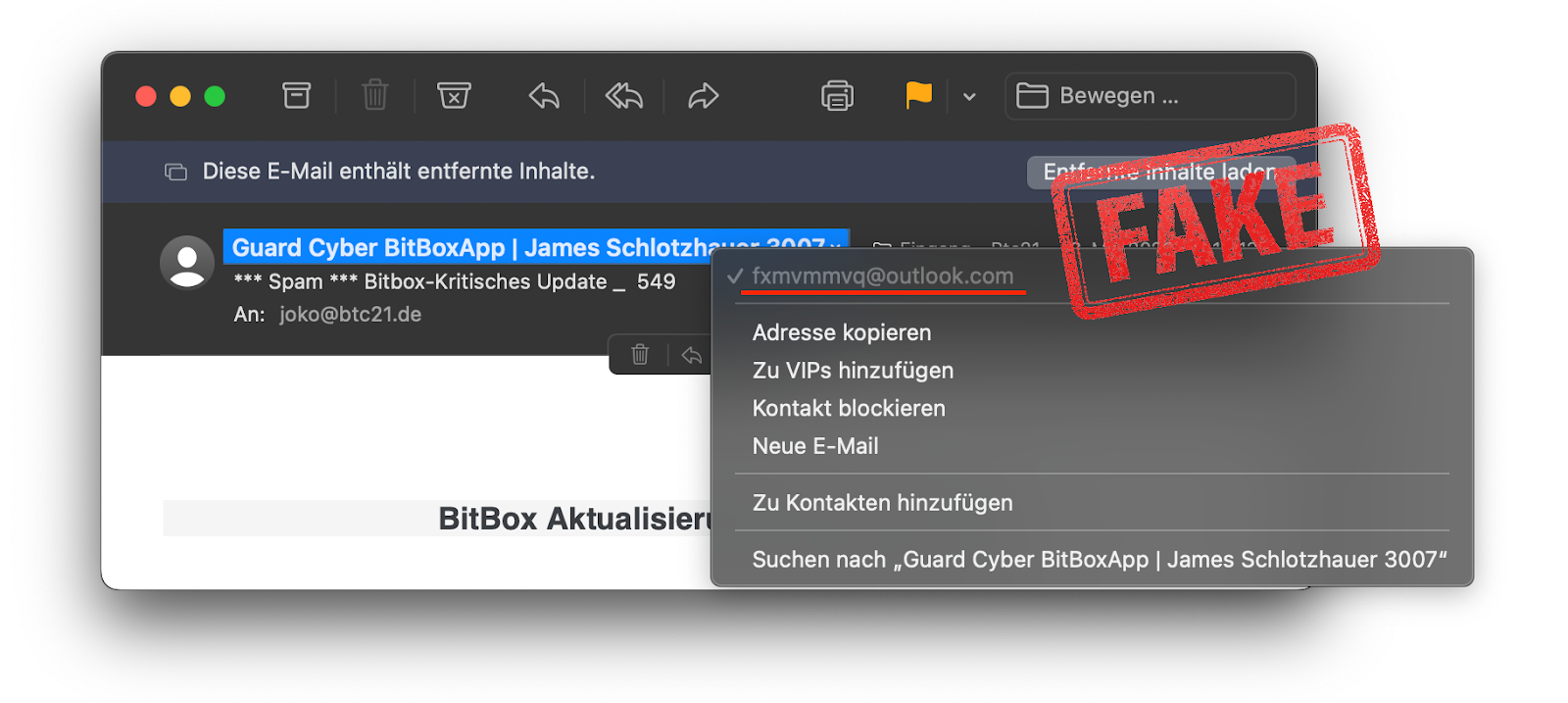
Read our more extensive article on how to protect yourself from scam emails.
Using keyloggers
Last but not least, we come to a more “classic” attack method that has been around for as long as we use keyboards: Keyloggers monitor inputs you make on your keyboard and forward them to an attacker. They can run in the background without raising suspicion or even outside the operating system of your computer – directly inside the keyboard’s firmware or remotely by intercepting its wireless communication.
While it may not be nice if a keylogger finds out what kind of emails you write to your colleagues, it would be catastrophic if you enter the 12 or 24 recovery words of your Bitcoin wallet directly on your computer – giving the attackers full control over the associated wallet. This is also one of many reasons why you should avoid using pure software based wallets (also known as “hot wallets”) for large amounts of money.
How to protect yourself
Apart from using a hardware wallet to protect yourself from key loggers in the first place, the most important rule is to never ever enter your recovery words anywhere other than directly on your hardware wallet. Make sure to store backups of your wallet in a secure and well hidden location, and never share them with anyone you do not fully trust with control over your wallet.
Conclusion
Reading through all of these attack methods and the way to protect yourself from them, it might all seem a bit difficult and scary. Is self-custody really that easy, if there are so many things to keep in mind to avoid making costly mistakes?
Well, if you look closely at all of the recommendations mentioned above – and those for other attack methods against users of hardware wallets out there – the core principles you have to follow to stay secure are actually quite simple. If you…
- Always verify all transaction details and receive addresses on the secure display of your hardware wallet.
- Never share your recovery words with anyone else, and only enter them directly on your hardware wallet.
… there is very little room for attackers to play with, and a lot of peace of mind for you and your bitcoin to gain!
Don’t own a BitBox yet?
Keeping your crypto secure doesn't have to be hard. The BitBox hardware wallets store the private keys for your cryptocurrencies offline. So you can manage your coins safely.
Both the BitBox02 Nova and the BitBox02 also come in a Bitcoin-only edition, featuring a radically focused firmware: less code means less attack surface, which further improves your security when only storing bitcoin.
Pre-order BitBox02 Nova or grab a BitBox02 in our shop!

Shift Crypto is a privately-held company based in Zurich, Switzerland. Our team of Bitcoin contributors, crypto experts, and security engineers builds products that enable customers to enjoy a stress-free journey from novice to mastery level of cryptocurrency management. The BitBox02, our second generation hardware wallet, lets users store, protect, and transact Bitcoin and other cryptocurrencies with ease — along with its software companion, the BitBoxApp!